For educational purposes only
https://github.com/knqyf263/dnspooq
Código:
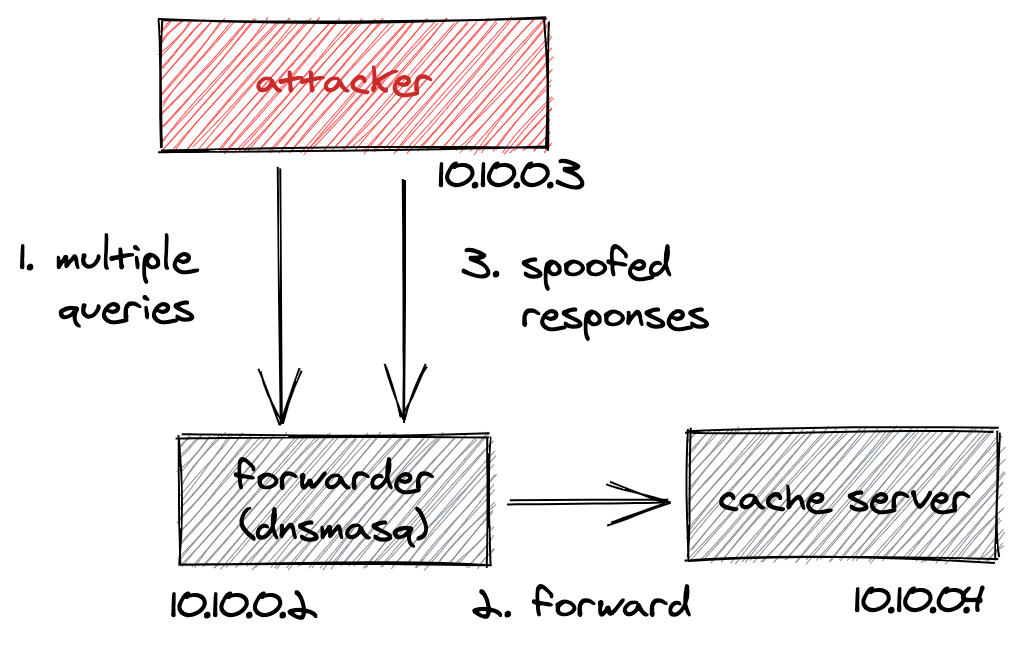
$ docker-compose exec attacker bash
bash-5.0# python exploit.py
exploit.py
Código





 Autor
Autor





 En línea
En línea

