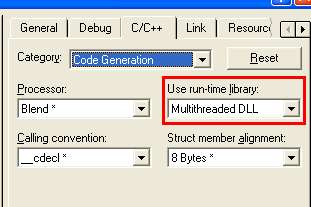
Como se compiló el ejecutable, para que sea dependiente de la DLL msvcrt
Como se buscó el export en la DLL, se puede observar su índice y su símbolo.

El resto del código no es nada especial, dejo el proyecto en vc6
http://www.mediafire.com/?s9vic23mvrjxrwg
Código:
//
// By 85
// elhacker.net
// InterceptAPI: (googleado en 5 segundos XD)
// 2013
//
#pragma comment (lib,"Shlwapi.lib")
#include<windows.h>
#include <Shlwapi.h>
#include<stdio.h>
///////////////////////////////////////////////////////////
char* mystrlwr(char* a){
static bool onlyonce=false;
if(!onlyonce){
onlyonce=true;
printf("\nSTRLWR INTERCEPTADA!\n");
// MessageBox(0,0,0,0);
}
return a;
}
//
BOOL InterceptAPI(HMODULE hLocalModule,const char* c_szDllName,const char* c_szApiName, DWORD dwReplaced)
{
DWORD dwOldProtect;
DWORD dwAddressToIntercept=(DWORD)GetProcAddress(GetModuleHandle((char*)c_szDllName),(char*)c_szApiName);
printf("add: %x\n", dwAddressToIntercept);
printf("dll: %s\n", c_szDllName);
printf("api: %s\n", c_szApiName);
// system("pause");
if(!dwAddressToIntercept) return false;
BYTE *pbTargetCode = (BYTE *) dwAddressToIntercept;
BYTE *pbReplaced = (BYTE *) dwReplaced;
VirtualProtect((void *) dwAddressToIntercept, 5, PAGE_WRITECOPY, &dwOldProtect);
*pbTargetCode++ = 0xE9; // jump rel32
*((signed int *)(pbTargetCode)) = pbReplaced - (pbTargetCode +4);
VirtualProtect((void *) dwAddressToIntercept, 5, PAGE_EXECUTE, &dwOldProtect);
FlushInstructionCache(GetCurrentProcess(), NULL, NULL);
return TRUE;
}
//
void Dummy(){
strlwr(new char[] = "85 de elhacker.net :D\0");
}
//
int main(){
Sleep(500);
char l_s11[] = {'m','s','v','c','p','6','0','.','d','l','l',0};
char l_s12[] = {'m','s','v','c','p','7','1','.','d','l','l',0};
char l_s13[] = {'m','s','v','c','p','1','0','0','.','d','l','l',0};
char l_s[] = {'m','s','v','c','r','t','.','d','l','l',0};
char l_api[] = {'_','s','t','r','l','w','r',0};
char l_exe[] = {'m','s','v','c','r','t','_','h','o','o','k','.','e','x','e',0};
char FileName[256];
if(!GetModuleHandle(l_s)) ExitProcess(0);
GetModuleFileName(GetModuleHandle(NULL), FileName, sizeof(FileName));
PathStripPath(FileName);
if (strcmp(FileName, l_exe) == 0){
InterceptAPI(GetModuleHandle(NULL), l_s, l_api, (DWORD)mystrlwr);
/* else: no se ha interceptado ! */
}
else
{ /* no se ha interceptado ! */ return 0;}
Dummy();
printf("\n");
system("pause");
return 0;
}





 Autor
Autor




 En línea
En línea

